没e也能玩
直接了当的dp,dq泄露攻击,不需要e
1 | p = getPrime(1024) |
直接流程解密即可
1 | c= |
flag{No_course_e_can_play}
格格你好棒
根据题目提示,可知应该是造个格就行
1 | flag = b'******' |
不等式的右边只有70,爆破即可
1 | from Crypto.Util.number import * |
flag{u_are@master_of_latt1ce_Crypt0gr@phy}
easy_ecc
基础的ecc,参数都全,没什么玄机
1 | p = |
求得m之后c1,c2除掉相应量即可
1 | from Crypto.Util.number import * |
flag{This_is_the_last_crypto_}
RSA?cmd5!
简单的签名过程
1 | # 什么 你说你用md5给rsa签名了 |
m='adm0n12'
1 | def get_flag(m0): # 请用这个函数来转m得到flag |
b’86133884de98baada58a8c4de66e15b8’ flag{th1s_1s_my_k3y:adm0n120xbfab06114aa460b85135659e359fe443f9d91950ca95cbb2cbd6f88453e2b08b}
故事新编1
使用网站解密 Vigenere Solver | guballa.de
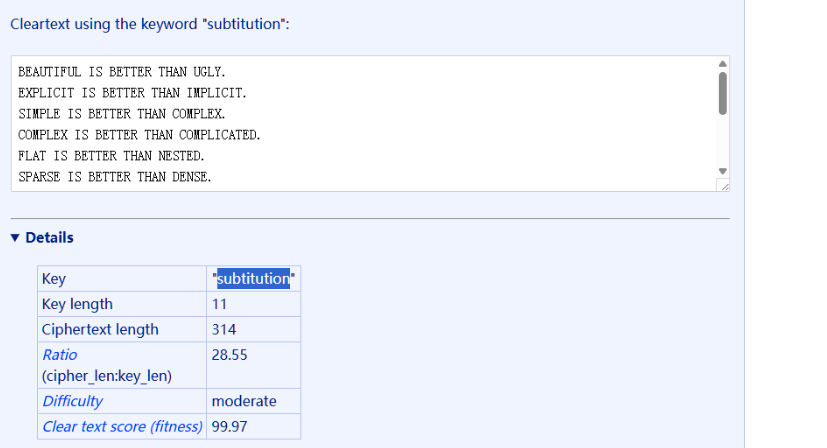
密钥为:subtitution
1 | from hashlib import md5 |
`flag{bda2bcf1eaeff7754a6483e74e70a937}
故事新编2
继续使用网站解密,模式改为AutoKey模式即可
密钥为:supersubtitution
1 | from hashlib import md5 |
flag{8bc383165248f2e45a6910960a61e6a8}
不用谢喵
查看题目发现encrypto是iv+enc,刚好是iv加两组CBC模式加密结果
给出decrypto为ECB模式下对encrypto的解密结果。
根据CBC模式的特点
将密文分为两组,enc1和enc2。两组ECB模式解密后分别是
1 | enc="f2040fe3063a5b6c65f66e1d2bf47b4cddb206e4ddcf7524932d25e92d57d3468398730b59df851cbac6d65073f9e138" |
flag{HOw_c4REfu1 Ly_yOu_O65ERve!}
没e这能玩?
解方程得到p,q,r。
离散对数得到e,解密即可
1 | pqr= [ ..., ... , ...] |
flag{th1s_2s_A_rea119_f34ggg}
两个黄鹂鸣翠柳
两个明文见存在线性关系,使用Franklin-Reiter-相关信息攻击即可,
大致原理在这篇文章中 相关信息攻击-Franklin-Reiter-CSDN博客
将其中爆破e的部分改为爆破t1,t2即可,大概20分钟左右解出
1 | from Crypto.Util.number import * |
这是几次方? 疑惑!
不知道为啥逆回去不对,把爆破一下得了
1 | c = 36513006092776816463005807690891878445084897511693065366878424579653926750135820835708001956534802873403195178517427725389634058598049226914694122804888321427912070308432512908833529417531492965615348806470164107231108504308584954154513331333004804817854315094324454847081460199485733298227480134551273155762 |
flag{yihuo_yuan_lai_xian_ji_suan_liang_bian_de2333}
Since you konw something
爆破key即可
1 | c=long_to_bytes(218950457292639210021937048771508243745941011391746420225459726647571) |
flag{Y0u_kn0w_th3_X0r_b3tt3r}
茶里茶气
tea加密,解密即可
1 | l = 199 |
flag{f14gg9_te2_1i_7ea_7}
Just one and more than two
多素数和单素数rsa解密即可
1 | e = 65537 |
flag{Y0u_re4lly_kn0w_Euler_4nd_N3xt_Eu1er_is_Y0u!}